When ransomware lands on your systems, your work life is likely to take a sudden and very precipitous nose dive. Between not being able to use your system or your data files and being told that you only have so much time -- maybe 72 hours -- to pay up or lose access forever, you'll end up having to make some fairly quick decisions and likely hoping afterwards that you did the right thing.
What exactly is ransomware?
Ransomware is a variety of malicious software that locks up your system or encrypts your files and then demands that a payment be made before the operation will be reversed. And, unfortunately, it's becoming more common and much more sophisticated. In the more advanced attacks, mid- and senior-level executives are now being targeted. In fact, the perpetrators often do enough research on their victims to make themselves appear to be more legitimate. They often take the time to learn people's proper names, titles, areas of specialization, etc. Any boost to the perpetrator's credibility will make it more likely that the intended targets see the attack as a legitimate request and act on it.
The cost of ransomware to individuals and businesses has amounted to many millions of dollars in recent years and is rising steeply. According to the FBI, the total just might reach $1 billion in 2016.
How does it get in?
Ransomware is generally delivered when someone clicks a link -- generally through email. This is called "spear phishing" or "whaling" (when the targets are high level staff). In fact, according to some accounts, the majority of phishing and whaling attacks today involve ransomware.
According to CSO online, 93% of phishing attempts involve ransomware. This is a staggering figure that attests to the success of this type of attack. For some ransomware attempts, perpetrators are well rewarded even if only 1% of their targets respond.
Some ransomware waits on web sites and not necessarily by design. Thousands of WordPress and Joomla! sites were compromised with CryptXXX just this June and July as reported in SecurityWeek.
How is it changing?
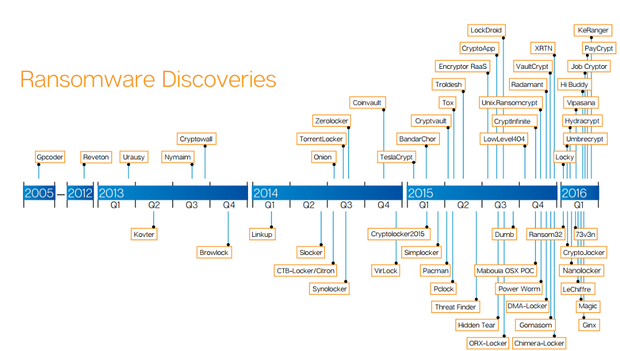
For one thing, the variety of ransomware (the software tools that are used) is escalating. The number of discovered ransomware tools has gone up dramatically since 2014. CERT-RO shared a graph depicting the varieties of ransomware that have been detected each year since 2005. The expansion is fairly overwhelming -- and this chart isn't necessarily up-to-date.
Another change is the focus on higher level targets. Ransomware attempts are no longer limited to going after any just computer or involving email with poor grammar being sent to tens of thousands of potential targets. In addition, very carefully crafted email is being sent to select targets with higher payoffs in mind. Grandma's family photos might still interest some hackers, but Grandma's medical records are likely to be of much more interest, particularly if Grandma's medical treatment might be derailed if the information is lost. The more someone might be willing to pay, the more likely they will be targeted.
Ransomware may lock your computers by encrypting all files or going after particular high interest files (e.g., spreadsheets, database files, and documents) or it may mess with your boot sector so that you can't get your system to work. If only select documents have been encrypted, you can sometimes identify what tool has been used by examining file extensions. This page at Bleeping Computer might help with identifying the tool that was used, but don't assume that the conventions will remain the same. Lucrative markets lead to new tools and practices -- on the "dark side" as well as in legitimate business.
Experts today sometimes refer to the ransomware perpetrators as being divided into two tiers. There's the "target everyone" level (those that might be interested in Grandma's photos) and there's the "go after the big guys" level (those that want big payoffs from a carefully selected group of people or organizations). Betsy Woudenberg from IntelligenceArts likens these two segments of attackers to lions and hyenas. The lions go after the big rewards while the hyenas go after anything they can get.
How bad is it getting?
Given that ransomware infections are becoming more costly, more sophisticated, and more complicated (many more varieties), and that there are many more attackers and a whole lot more money involved, no one in the field is expecting anything to get better any time soon. The field is expanding, larger amounts are being demanded, and payments are often required to be in bit coins (not linked to particular individuals). In addition, there are tools that security experts are calling RaaS for "ransomware as a service". And much like the "script kiddies" who appeared many decades ago, technically clueless people can find tools that facilitate their attacks -- without ever having to take any deep dives into the technology.
Should you pay?
The best advice is probably to not pay. However, each organization has to consider what the loss will likely be to them and whether they can take the hit. Paying essentially means that you are promoting the activity. According to the experts, most of the time paying the ransom will result in your data or access being recovered. If this were not the case, targeted individuals would stop paying and that wouldn't work very well for those orchestrating the attacks. However, there's no saying that they won't come back again. And some attackers have gone as far as asking for a second payment, holding off on the promised decryption, even after the requested payment was made.
Getting help
There are some avenues for getting help. Some organizations are actively working to provide tools to help reverse the damages caused by ransomware. One such organization -- NoMoreRansom -- is worth checking. This Windows Club site provides information on other tools for recovering your data. But don't expect magic. In many cases, all you can hope for is that you can get your hands on the proper key to decrypt your files.
You can also reach out to the FBI and Secret Service for advice and assistance in possibly tracking down how your attacker was able to get in and cause the damage. Here are some URLs to help you get started:
https://www.fbi.gov/contact-us/field-offices
https://www.secretservice.gov/investigation
Questions to ask yourself today
Don't just sit there and hope that you won't be targeted by ransomware. You should be asking yourself some hard questions today.
- How can you prevent ransomware from getting to your systems?
- If an asset is attacked, how can you work around the problem?
- How much time will you need to recover?
- How critical are your information assets? Which are most critical? Which are most vulnerable?
- How can you train the people in your organization who are most likely to be targeted to avoid inviting the ransomware in?
- Which of your business practices help you avoid ransomware infections and which of your business practices make it harder to ward off ransomware?
- What plans do you have for business continuity? Have they been tested?
- Can you fall back to paper files or manual procedures?
- Who will you need to call if ransomware attacks your systems?
Precautions you should take
There are also things that you should be doing routinely.
- back up your files every night and practice recovery
- protect your backups from any possible attack vector (air gap? off network?)
- train your staff, especially those who are likely to be targeted -- no matter how high level they might be
- document your anti-ransomware strategies and make sure your plans are implemented
Is there light at the end of the tunnel?
Some, but there's a lot of dark in there too. The best things you can do right now are to think seriously about your options for business continuity and work on both training your staff and protecting your critical assets.