Originally published on Webroot
Edited by Nero Consulting
As the impact and severity of crypto-ransomware threats and attacks has grown over the past 2½ years, we have published many blogs and articles on how best to defend against these modern day extortionists. We do not believe that our businesses or consumer customers should have to choose between extortion and losing precious, irreplaceable data. We often get asked the leading question: “which endpoint security solution will offer 100% prevention and protection from crypto-ransomware?” The simple answer is none. Even the best endpoint security will only be 100% effective most of the time. At other times the cybercriminals will have found ways to circumvent endpoint security defenses and their attack will likely succeed. Each day many ransomware campaign operators create a new variant which is re-packed making it once again undetected for all of antivirus.
- Use Reputable, Proven, Multi-Vector Endpoint Security
- Back-up your data.
- Your main storage area (file server)
- Local disk backup
- Mirrors in a cloud business continuity service
- User Education.
- Disable execution of script files.
- Patch and keep software up to date.
- Secure weak username/passwords which have Remote Desktop access.
Nero uses and recommends Webroot exclusively because Webroot has built a strong reputation for stopping crypto-ransomware. Webroot was the first antivirus and antimalware vendor to move completely away from the standard, signature-based file detection method. By harnessing the power of cloud computing, Webroot replaced traditional, reactive antivirus with proactive, real-time endpoint monitoring and threat intelligence, defending each endpoint individually, while gathering, analyzing, and propagating threat data collectively. This predictive infection prevention model enables Webroot solutions to accurately categorize existing, modified, and new executable files and processes, at the point of execution, to determine their status.
Of course, you need protection that covers multiple threat vectors. For instance, real-time anti-phishing to stop email links to phishing sites, web browser protection to stop browser threats, and web reputation to block risky sites that might only occasionally be unsafe. Over the past four years, the Webroot approach to infection prevention has continuously proven its efficacy at stopping crypto-malware in real time by addressing threats the moment they attempt to infect a device, stopping the encryption process before it starts. Regardless of which endpoint security solution you choose, it’s essential it offers multi-dimensional protection and prevention against malware to ensure it quickly recognizes external threats and any suspicious behaviors. A next-generation endpoint security solution with protection beyond file-based threats is essential.
If you have failed to stop ransomware from successfully encrypting your data, then the next best protection is being able to restore your data and minimize business downtime.
Bear in mind when you are setting up your backup strategy that crypto-ransomware like CryptoLocker will also encrypt files on drives that are mapped, and some modern variants will look for unmapped drives too. Crypto-ransomware will look for external drives such as USB thumb drives, as well as any network or cloud file stores that you have assigned a drive letter to.
You need to set up a regular backup regimen that at a minimum backs up data to an external drive, or backup service, that is completely disconnected when it is not performing the backup.
The recommended best practice is that your data and systems are backed up in at least three different places.
In the event of a ransomware disaster, this set-up will give you the ability to mitigate any takeover of your data and almost immediately regain the full functionality of your critical IT systems.
The “human firewall” – the endusers – are often the weakest security link.
If a user receives an invoice, receipt, or any other form of attachment from someone they are unfamiliar with, chances are it’s bad. For word document emails, it is also advised to warn users to avoid clicking “enable content” for emails from unfamiliar sources.
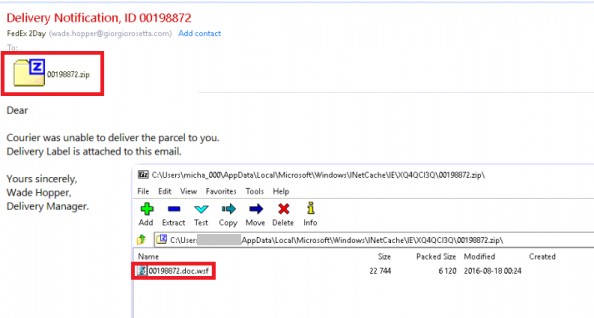
Ransomware such as Locky (.thor), Nemucod (.crypted), and Cerber are most often delivered via spam email. This spam email contains an attached zip archive. After the user opens the zip archive, there’s a script or a macro enabled office document and when opened, the ransomware payload is downloaded and executed.
Example Spam Email:
In order to prevent these types of documents and scripts from running we recommend speaking to your IT Admin or reach out to Nero Consulting for guidance & assistance.
Ransomware such as: CryptMic, CryptXXX, Cerber, and Locky can be distributed via exploit kits, which target the software vulnerabilities of Adobe Flash Player, Oracle Java, Internet Explorer, Microsoft Silverlight and other vulnerable applications. If this software is exploited, an exploit kit landing page can execute arbitrary code and initiate a silent drive by download. It is critical for system administrators to keep this type of software up to date as most infections dropped by Exploit Kits are known as "zero days" (malware which is fully undetected by all antivirus). If outdated software must be present in your environment, we recommend you download and install Microsoft's EMET to mitigate attacks.
Cybercriminals scan the internet daily for systems with commonly used RDP ports and bruteforce with weak usernames/passwords and attempt to gain access. Once access has been gained, they can deploy variants of ransomware, create user accounts, and download other unwanted malicious software.
For some tips on how you can use to help secure RDP and prevent this type of attack we recommend speaking to your IT Admin or reach out to Nero Consulting for guidance & assistance.