It makes a lot of sense for electronics firms to pack a variety of functions into mobile devices and expand their usefulness. Instead of confining their use to communications, companies such as Apple, Samsung, and others have turned mobile phones into mini-computers that can serve as a substitute for your laptop, or as a storage device.
Reasons to back up your mobile devices
No Ransom: a place for free decryption
Fileless malware: who are the targets?
Statistics for cyber security during 2016
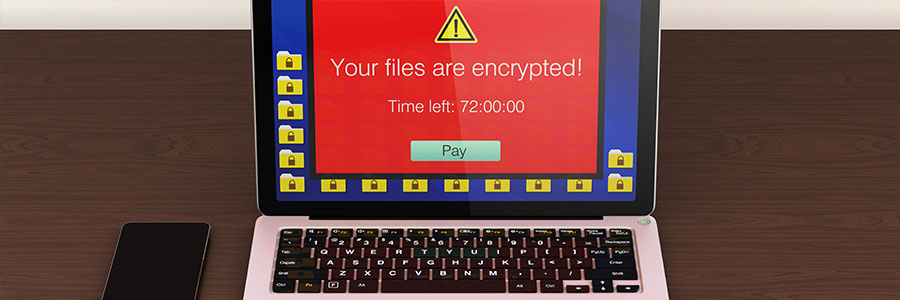
The ransomware that makes you sell your soul

Ransomware has become a fast-track for making money for some hackers this holiday season. But instead of just demanding a small payment for the decryption code that will unlock their computers, some hackers are demanding that victims sacrifice two other friends to ensure they receive the code they need.
The benefits of internet monitoring
9 cybersecurity terms everyone must know

Everyone, from doctors to lawyers, needs to continue learning to stay ahead of the times. Business owners might have it worst of all, oftentimes needing to stay on top of several industries to keep their company running. Keep reading for a refresher on all the latest trends and buzzwords used in the cybersecurity sector.
4 BYOD security risks you should address
7 Warning signs of malware infection
Browser Extensions and Online Privacy

Think you’ve got enough security measures in place within your company? How do you know what the next malware release will bring? Do you trust your employees implicitly? Of course you do - you hired them and they’re a good bunch of people! But even the nicest guy may inadvertently visit a website that’s been infested with viruses or fall victim to a cunning phishing scam.