If you have an Android device, be careful! An exceptionally dangerous Android malware known as DEFENSOR ID is currently making the rounds in the Google Play Store. The malware exploits the Accessibility Services in an Android device to evade detection by traditional security measures.
How to enable windows defender? Support for New York Businesses
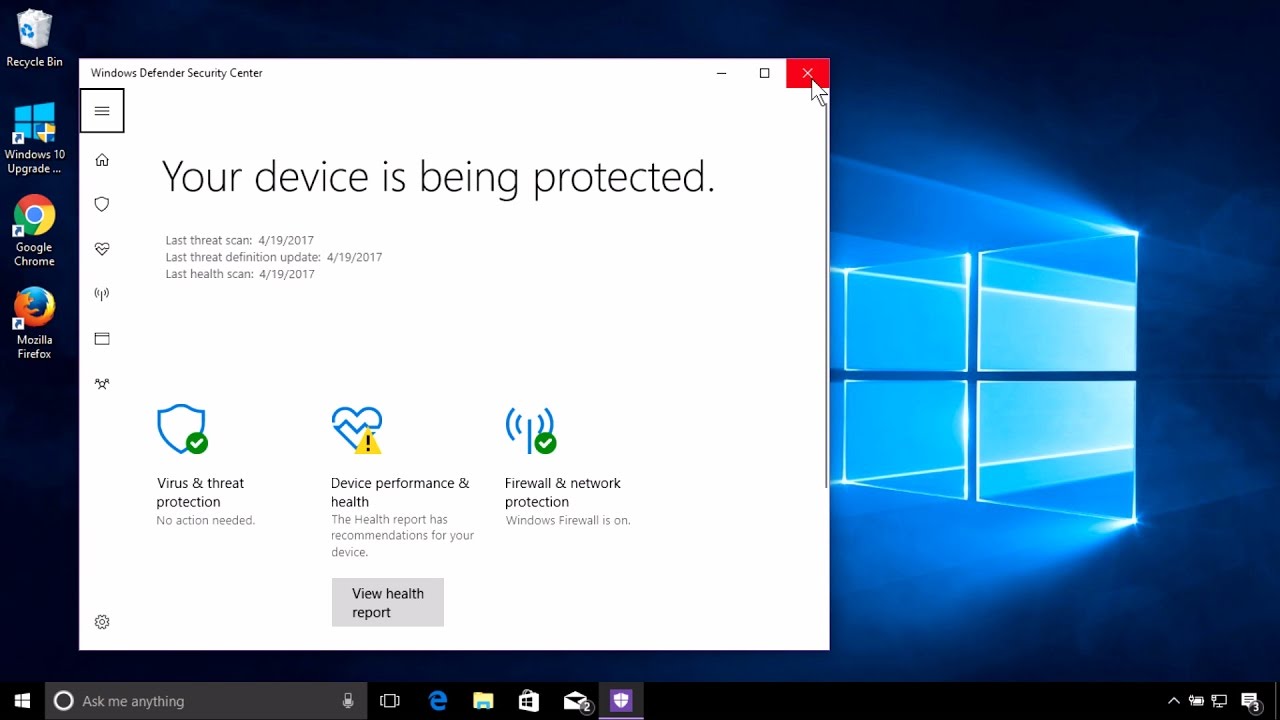
Here is a quick overview for how to enable Windows Defender in your Windows 10 devices:
Open the taskbar
Click the Windows Defender Icon (Shield or Castle depending on O.S)
This will open the Windows Defender Panel. Here look for the setting “Turn off Windows Defender Antivirus” which is underneath the folders of other settings.
Are your business printers protected against hacks?
Keep these in mind when shopping for antivirus software
Security best practices for remote workers
VPN: A quick way to secure remote work connections

A lot of us are suddenly working from home, but few are taking enough safety precautions. Remember, cybercriminals may take advantage of these circumstances to attempt to infiltrate organizations.
So, how can we make sure our sensitive data remains encrypted and secure?
The answer: get a Virtual Private Network (VPN).
VPN is part of a layered security plan and it’s particularly useful for granting remote access safely.
Technology Checklist for SMB’s now Working from Home

You’re home and you’re working. The same goes for your team, and this means everyone.
It won’t last forever (we hope), but it is going to be a little while until we get back to normal.
Your IT department or partner is probably going at 110% right now as they get each person ready to work from home, and they are going to deserve a prize when things settle down.
Autocomplete password risks

Web browsers come with features to improve user experience. One of the most popular ones is auto-fill passwords. These are designed for users to store and automatically use their account credentials to access websites and other applications. While auto-fill passwords are convenient, they come with security risks.







